Cybersecurity 101 – 2MFA, MFA (Multi-Factor Authentication)
What is multi-factor authentication?
Multi-Factor Authentication (MFA) is a security system that requires users to confirm their identity using two or more verification methods before gaining access to accounts, applications, or systems. It enhances security by combining:
· Knowledge: Information the user knows, like a password or PIN.
· Possession: Something the user physically has, such as a security token or smartphone.
· Inherence: A unique trait of the user, like their fingerprint or facial recognition.
You may sometimes see MFA referred to as two-factor authentication (2FA), which is, unsurprisingly, where two factors are used. This layered approach protects against unauthorized access by requiring multiple forms of proof, making it far more secure than relying on passwords alone.
Analogy: A Multi-Layered Lock
Consider entering your house with a key. If someone steals your key, they could easily access your home. However, if the door also required a fingerprint scan or a PIN code, the theft of the key alone would not grant entry. Similarly, MFA applies multiple verification steps to protect sensitive systems.
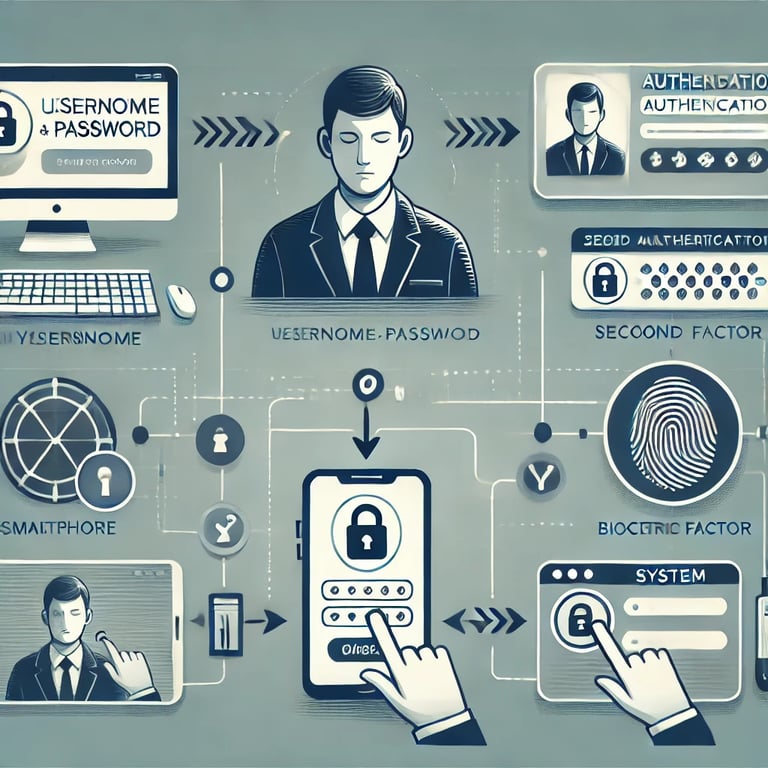
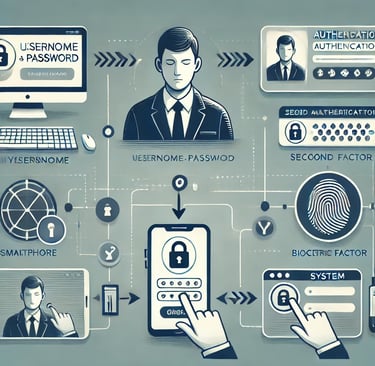
How MFA Works
Login Attempt: The user enters their username and password.
Second Factor: After password verification, the system prompts for a second factor (e.g., a code sent to the user's phone).
Access Granted: If the second factor is verified, the user gains access.
Benefits of MFA
Improved Security: Safeguards against stolen credentials and phishing attacks.
Regulatory Compliance: Meets standards like GDPR, PCI DSS, and HIPAA.
Risk Reduction: Prevents account takeovers and enhances overall system safety.
Ease of Use: Modern MFA solutions, like app-based push notifications, simplify the process for users.
Major platforms like Google and Microsoft report that MFA can prevent the majority of account hacks. While some users find MFA slightly inconvenient, its security benefits far outweigh the effort required.
Types of MFA
There are three common types of factors used for MFA:
· Knowledge: Passwords or PINs.
· Possession: Physical items like smart cards, security tokens, or apps such as Google Authenticator.
· Inherence: Biometrics such as fingerprints, facial recognition, or voice authentication.
Implementing MFA and securing your data is now easier than ever. You may even use it today as part of your online purchases, or when logging in to your online bank.
Best Practices for MFA Implementation
Choose Reliable Methods: Prefer authenticator apps over SMS, as SMS can be intercepted.
Educate Users: Teach users how to use MFA effectively and why it matters.
Backup Options: Provide alternative methods in case the primary factor is unavailable.
Examples of MFA Tools
Authenticator Apps: Google Authenticator, Microsoft Authenticator, Duo Security, etc.
Hardware Tokens: YubiKey, RSA SecurID.
Biometric Devices: Fingerprint scanners, Face ID.
SMS/Email Codes: OTPs sent via text or email.