Cybersecurity 101 – Social Engineering and Phishing Emails
Social Engineering 101
Perhaps you have heard this term before. Social engineering encompasses a range of methods aimed at influencing people to reveal sensitive information, perform certain actions, or make decisions they normally wouldn’t. It relies on psychological manipulation, taking advantage of human nature, trust, and decision-making habits, making it challenging for individuals to spot the deception.
Social engineers exploit people's motivations and fears, guiding them into actions that serve the attacker’s interests.
Why is it Important to Guard Against Social Engineering Attacks?
Social engineering poses serious risks to individuals, businesses, and even governments. Past incidents show that these types of attacks can cause significant harm to organizations.
By leveraging human behavior, social engineering is highly effective. Attackers can trick or pressure individuals into giving up confidential information, clicking on malicious links, or engaging in other actions that compromise security.
Because it targets human vulnerabilities, social engineering can often bypass traditional security measures, like firewalls and antivirus programs.
What Are Social Engineers Looking For?
Social engineers usually aim to gain access to valuable information such as login credentials, personal data, financial details, or intellectual property. This data can be exploited for identity theft, financial fraud, corporate espionage, and more.
Once inside a network, attackers may launch further attacks, leading to data breaches or service disruptions.
Potential Consequences of Social Engineering Attacks
A key goal of social engineering is financial gain, and attacks can result in major financial losses from fraud, identity theft, or other harmful activities. Despite strong data security protocols, social engineering may lead employees to inadvertently disclose sensitive information. Failure to protect this data can result in legal and regulatory consequences, particularly in areas with strict data protection laws.
These attacks can also damage an organization’s reputation, leading to a loss of trust from customers, partners, and stakeholders. For individuals affected, the experience can be mentally distressing. The most basic and most prevalent form of social engineering attack is what we call “Phishing”
Understanding Phishing
What is Phishing?
Phishing is a specific form of social engineering designed to steal confidential information, such as login credentials or bank details. By pretending to be a legitimate organization or person, attackers trick individuals into performing actions like transferring funds or downloading malware through harmful links or attachments.
While phishing is often conducted through email, it can also occur in other forms such as but not limited to
via phone calls ("vishing"),
text messages ("SMShing"),
social media,
messaging apps
QR code or “Qishing”
Others
A common variant, known as business email compromise (BEC), involves attackers using genuine corporate email accounts to request fake payments, typically targeting executives or budget handlers.
Common Traits of Phishing Emails
Phishing emails are specially crafted to evoke emotional responses, often prompting recipients to click malicious links or download attachments that lead to fake websites or install harmful software. To provoke a reaction, attackers commonly use tactics such as but not limited to:
Promises of rewards, like gift cards or prize winnings.
Impersonation of authority figures, such as government officials or company leaders, often using specific information about the organization.
Intimidation tactics, suggesting negative outcomes if an action isn’t taken.
A sense of urgency, creating pressure to act fast.
Social proof, implying that others have already responded or acted.
Enticing document titles, like “Payslip” or “Invoice.”
Building trust by pretending to be someone familiar to the recipient.
How to Protect Yourself from Phishing/Email Scams
Remaining vigilant is the best way to detect phishing attempts. Here are a few strategies to protect yourself:
Carefully check sender details for unknown or suspicious email addresses.
Hover over links to verify that URLs are legitimate and match the intended source.
Be cautious with unexpected emails—if it’s unsolicited, it’s safer to ignore it.
Not because it does not contain any links or attachment means it is already safe, some utilize social engineering tactics like blackmailing to extort money.
If something seems too good to be true, it probably isn’t!
Phishing and Scam Email Examples
*Paypal phishing email
*Account termination scams
*Blackmail and extortion – this is very popular back in the day and even up to now
I could go on with countless examples but I hope you learn something from above given ones. Stay safe online!
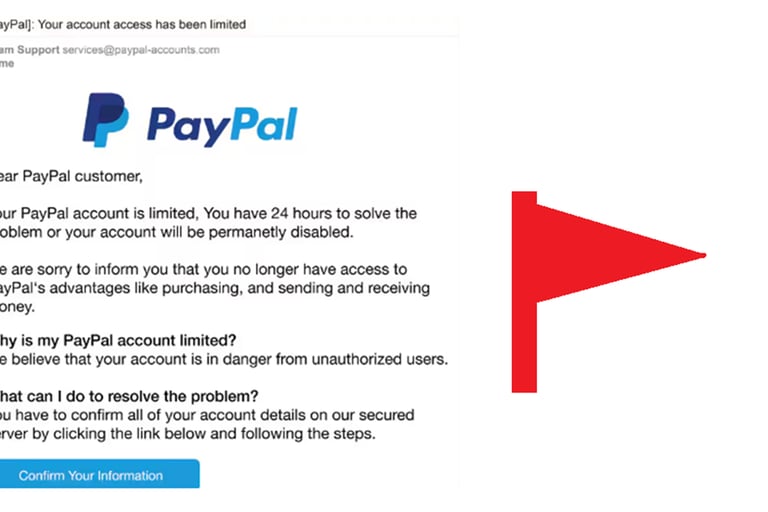
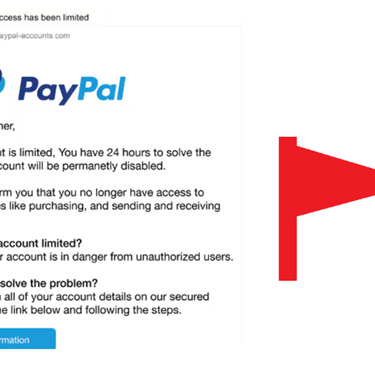
Red Flags:
From email address is not the legitimate email from paypal
There is sense of urgency.
Person being addressed is generic hinting this was sent to many.
Grammar issues on the mail content.
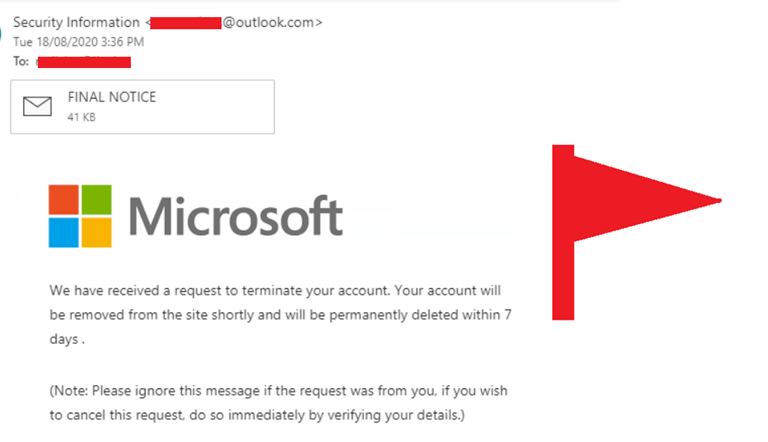
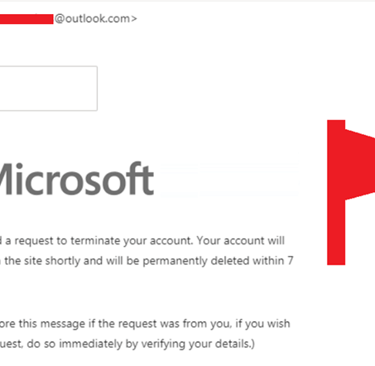
Red Flags:
1. Again notice there is sense of urgency.
2. Email is very generic.
3. There is a suspicious attachment.
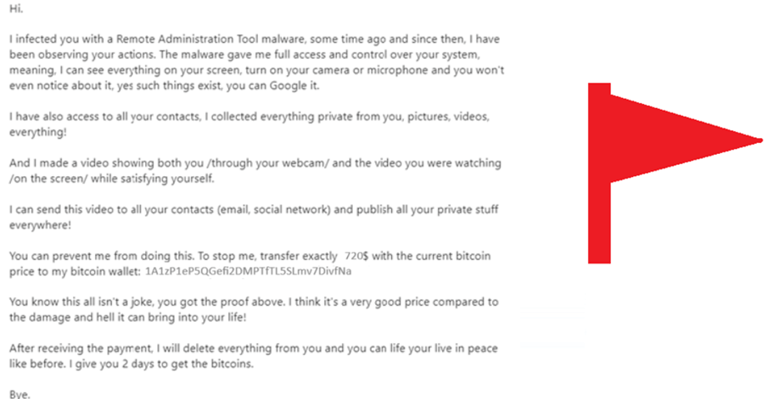
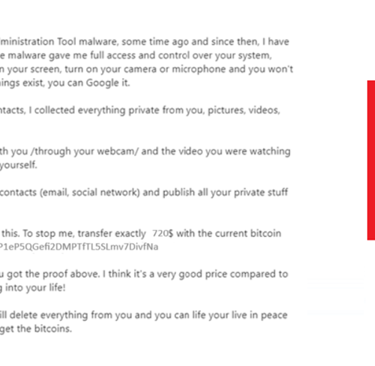
Red Flags:
1. Very generic salutation
2. Notice no links or attachments but;
3. It’s message is clearly blackmailing the victim to lay in bitcoin or else.
4. Clearly an attempt to social engineer someone to give money.