DFIR vs. Threat Hunting: Key Differences
Explore the fundamental differences between Digital Forensics and Incident Response (DFIR) and Threat Hunting. Understand how DFIR focuses on reacting to detected incidents with investigation and recovery, while Threat Hunting takes a proactive approach to uncover hidden threats before they cause damage. Learn how both practices complement each other to strengthen cybersecurity defenses.
THREAT HUNTINGDFIR
5/8/20242 min read


DFIR vs. Threat Hunting: Key Differences
Introduction
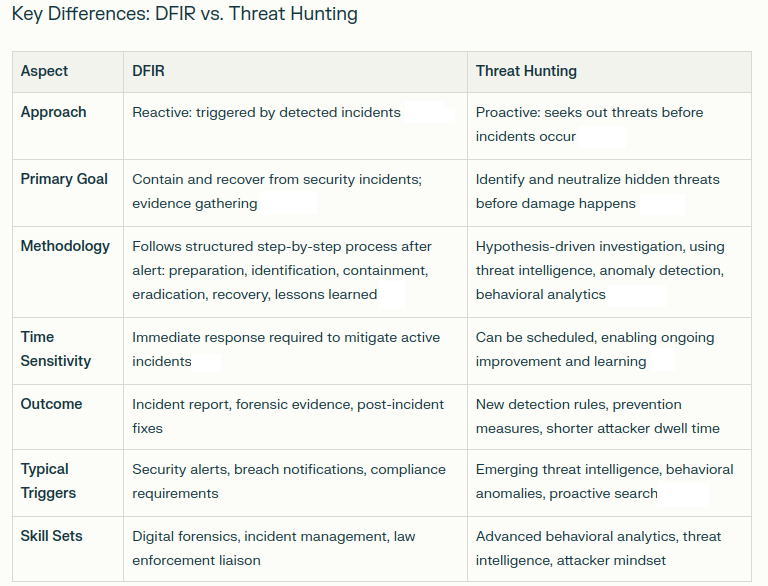
Digital Forensics and Incident Response (DFIR) and Threat Hunting are essential practices in modern cybersecurity. While both aim to defend organizations against cyber threats, they approach the challenge in distinctly different ways. Understanding their roles, methods, and objectives is crucial for anyone responsible for security—or aspiring to join the field.
What Is DFIR?
Digital Forensics and Incident Response (DFIR) is a discipline that encompasses two primary activities:
Digital Forensics: The process of collecting, preserving, analyzing, and presenting digital evidence following a security incident.
Incident Response: A structured approach carried out after a security incident or breach is detected, focusing on containing, eradicating, and recovering from the attack
.
DFIR is fundamentally reactive—it is triggered by the detection (or strong suspicion) of an incident and is designed to minimize damage, restore operations, and document evidence for legal or regulatory needs.
What Is Threat Hunting?
Threat Hunting is the proactive pursuit of hidden or unknown threats within an organization’s environment
. Rather than relying solely on alerts, threat hunters assume attackers may already be in the system. They actively search for indicators of compromise (IOCs), tactics, techniques, and procedures (TTPs), or anomalous behaviors that evade traditional security controls.
Threat hunting is hypothesis-driven, investigative, and designed to prevent incidents before they occur by uncovering stealthy adversaries and their methods
How They Complement Each Other
Threat hunting helps find attackers who evade conventional security controls, potentially allowing organizations to detect threats before they inflict serious harm.
DFIR activates when signs of compromise are found—whether by threat hunting, automatic alerts, or outside notification—to contain, investigate, collect evidence, and remediate
Both practices feed into each other: effective threat hunting can reduce the number of serious incidents requiring full response, and insights from DFIR investigations can inform better threat hunting strategies
When to Use Each
Threat Hunting should be a continuous or regularly scheduled operation, especially for organizations facing advanced persistent threats (APTs) or targeted attacks.
DFIR engages whenever an incident is confirmed or strongly suspected, ensuring that the organization can contain, eradicate, and recover while preserving crucial evidence.
Conclusion
DFIR and Threat Hunting are both vital in a robust cybersecurity strategy, but their focuses differ:
DFIR reacts to incidents and is centered on investigation, evidence, and recovery.
Threat Hunting proactively seeks threats that may have slipped past defenses, aiming to intervene before incident response is required.
Integrating both approaches ensures not only faster detection and resolution of threats, but also a more resilient security posture overall