What Happens in a Typical Incident Response Lifecycle?
Discover the key phases of the incident response lifecycle—from preparation and detection to containment and recovery. This post breaks down each step to help you understand how organizations effectively manage cyber incidents, minimize damage, and improve security posture for the future.Blog post description.
DFIR
7/25/20253 min read
What Happens in a Typical Incident Response Lifecycle?
In cybersecurity, responding swiftly and effectively to incidents like breaches or malware infections is crucial to minimize damage and restore normal operations. The Incident Response Lifecycle is a structured approach organizations use to manage such events, ensuring consistency and efficiency from preparation to recovery. The most widely accepted model comes from the National Institute of Standards and Technology (NIST), which divides the lifecycle into clear, actionable phases.
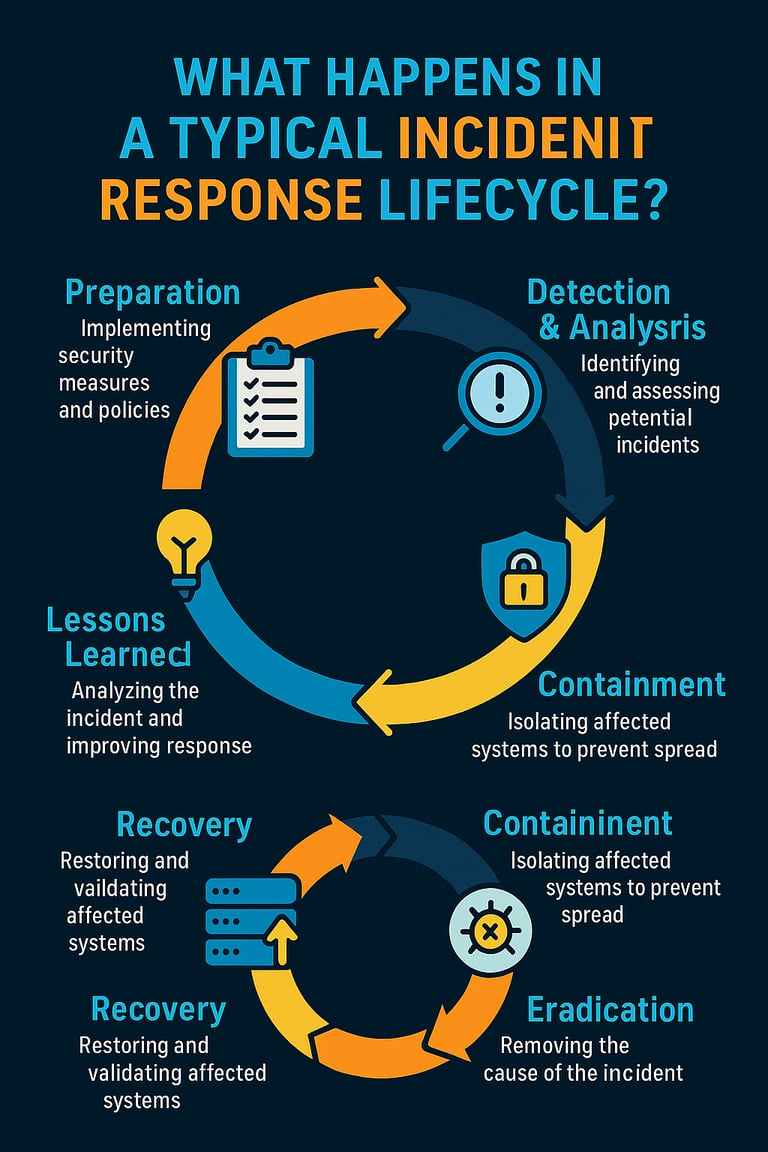
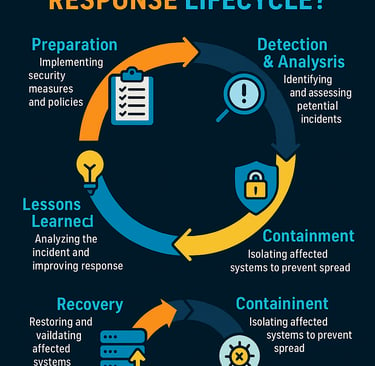
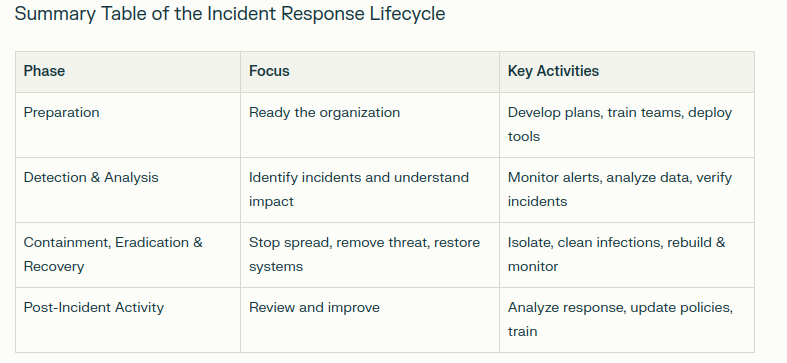
Here’s a detailed breakdown of what happens in a typical incident response lifecycle:
1. Preparation
Preparation lays the groundwork for all incident response activities. It involves establishing and maintaining the policies, tools, and teams required to detect and manage incidents. Key tasks include:
Creating an incident response (IR) plan that defines roles, responsibilities, and communication channels.
Training the incident response team and relevant staff.
Conducting risk assessments and identifying critical assets.
Implementing security controls such as logging, monitoring, and alerting systems.
Ensuring proper tools (for forensic analysis, malware detection, etc.) are deployed and updated.
This phase is essential because it enables teams to act quickly and decisively when incidents occur, minimizing confusion and delays
2. Detection and Analysis (Identification)
This phase is triggered by events or alerts suggesting a security incident. The goals are to detect the incident promptly and analyze it to understand its nature, scope, and impact. Activities include:
Monitoring logs, alerts, and network traffic to spot anomalies or breach indicators.
Collecting and analyzing data such as system logs, malware samples, and network connections.
Classifying the type of attack (e.g., ransomware, phishing, DDoS).
Assessing affected systems and user accounts to measure damage or risk.
Correctly distinguishing between true incidents and false positives is critical here to allocate resources effectively
3. Containment, Eradication, and Recovery
This combined phase is the operational core of incident response and is executed swiftly to limit damage and restore normalcy.
Containment: Actions focus on isolating affected systems to prevent the incident from spreading. This might include disconnecting compromised devices from the network, blocking malicious IP addresses, or quarantining malware infections.
Eradication: The root cause (e.g., malware, vulnerabilities, unauthorized access) is removed from the environment. This may involve cleaning infected files, patching systems, or disabling compromised accounts.
Recovery: Systems and services are restored to their normal and secure state. This could involve restoring data from backups, rebuilding systems, and monitoring for any signs of residual malicious activity.
The goal is not only to eliminate the immediate threat but also to restore business operations safely and swiftly
4. Post-Incident Activity (Lessons Learned)
Once the incident is fully resolved, this final phase involves reviewing the entire response process to identify strengths, weaknesses, and improvement opportunities. Key actions include:
Conducting a detailed post-mortem analysis and documenting lessons learned.
Updating incident response plans, security policies, and controls based on findings.
Providing additional training or awareness programs if needed.
Implementing preventive measures to reduce the likelihood of a similar incident recurring.
This phase strengthens future readiness and ensures continuous improvement for the organization’s security posture
Why Following the Incident Response Lifecycle Matters
Handling cyber incidents can be chaotic and high-pressure. The lifecycle model ensures a clear, consistent, and thorough approach—helping organizations:
React faster and more effectively
Minimize operational and financial impact
Preserve critical evidence for compliance or legal action
Learn and evolve their defenses over time
Final Thoughts
The incident response lifecycle provides a trusted framework to manage cybersecurity incidents effectively. By mastering each phase, security teams can reduce risk, protect assets, and strengthen their organization’s resilience against the ever-growing landscape of cyber threats.
References:
EC-Council, NIST Incident Response Life Cycle (2025)
TitanFile, 7 Phases of Incident Response (2024)
Atlassian, Incident Response Lifecycle (2021)
